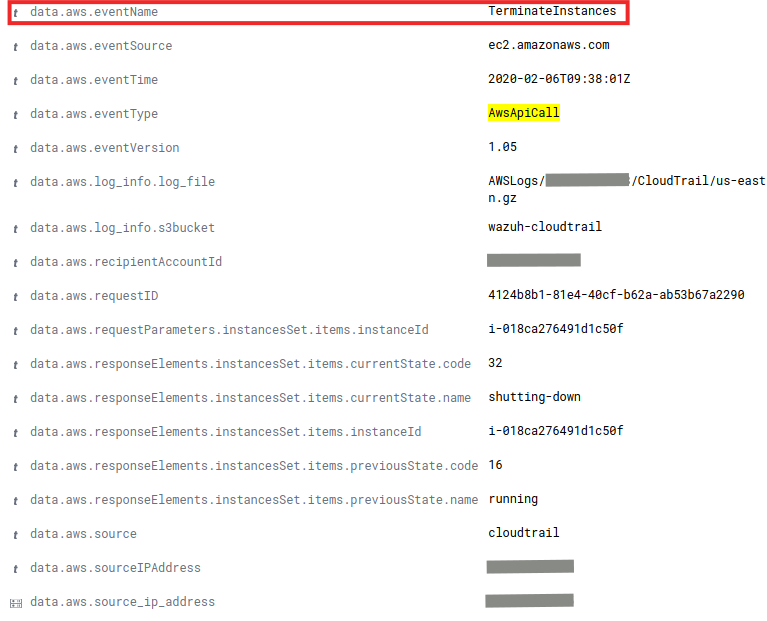
Amazon offers many tools to monitor the status of its services. A good example is Amazon Macie, aimed at the surveillance of stored data. This is a resource of enormous relevance in recent times and therefore it requires its correct treatment and protection.
There is no doubt that in order to protect the data, we must have a properly guarded system that is free from intruders and security breaches which could lead to improper access. Wazuh and its wide community provide the necessary tools in this regard.
If we have to access a different dashboard for each service we use (Amazon CloudTrail, Macie, GuardDuty, File Integrity Monitoring, etc.), the task becomes more difficult to carry out. Therefore, this time we are going to undertake the integration of Amazon Macie alerts in Kibana thanks to Wazuh, centralizing all the security information that we have in a single point.
Amazon Macie
Amazon Macie is a service responsible for detecting and classifying suspicious activities, intellectual property and unprotected personal or confidential data within S3 buckets. It uses machine learning to carry out those tasks and generates alerts that help the administrator to discover possible problems; Problems which could lead to exposure of data or even the loss of it.
The Amazon Macie activation process is fairly straightforward. You just have to follow a few steps that you can find detailed in its official guide.
Please note that in order to integrate events into Wazuh, they must be accessible from an S3 bucket. Macie by itself does not offer the possibility of storing the logs generated within it. In consequence, it is necessary to activate Amazon Kinesis, a tool that makes it easy to collect and save those logs in a bucket. Once this is done, Wazuh will read them and display the data in Kibana. You can find a detailed guide on how to activate Amazon Kinesis in our documentation.
Sending logs to Wazuh
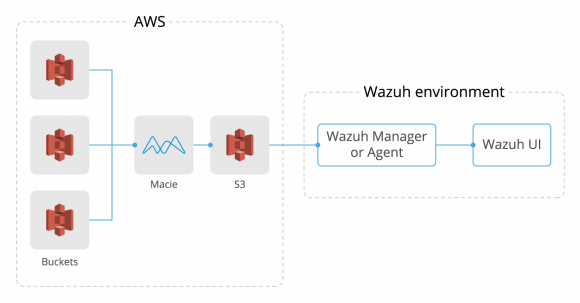
The workflow from the moment Amazon Macie generates events until they are displayed in the Wazuh UI is quite simple. First, Macie analyzes each configured bucket and generates the events based on the problems it finds, it then stores those events in a different bucket. Secondly, Wazuh will access that bucket to collect all the information stored there. The Wazuh AWS module saves in a database which logs have already been read, thus avoiding downloading the same event several times. At this point, if we add custom rules, alerts will be generated based on criteria that we ourselves establish.
We can also automate the execution of any action with integratord. For example, if we use it together with Boto3, it can automatically block any IP that is trying to access our S3 without permission. To configure this behaviour we can follow the example described in our post Monitoring AWS environments with Wazuh.
Finally, we can access the Wazuh UI to query those alerts. The following diagram represents, in summary, the flow that we have just described.
Setting up Wazuh AWS module
Once Macie logs are stored in a bucket, it’s time to set up the AWS module in the Wazuh configuration file in order to collect them. Access the Wazuh agent (or manager) that will be in charge of this task, edit the configuration file <WAZUH_HOME>/etc/ossec.conf and add the following code block:
<wodle name="aws-s3">
<disabled>no</disabled>
<interval>10m</interval>
<run_on_start>yes</run_on_start>
<skip_on_error>yes</skip_on_error>
<bucket type="custom">
<name>wazuh-aws-wodle</name>
<path>macie</path>
<aws_profile>default</aws_profile>
</bucket>
</wodle>
Remember that, as we already explained in our post Using CloudTrail to monitor AWS activity and in the documentation, you will need to add the AWS access credentials in a file located at ~/.aws/credentials. You can also find more detailed information about each AWS module configuration parameter in our documentation.
Note: It is possible to specify the credentials within the wodle configuration in ossec.conf. However, we do not recommend this option.
Now you only need to restart Wazuh and it will start reading the logs from Macie.
Checking if it works
Possibly, the easiest way to check that Macie alerts are being collected and processed correctly in Wazuh is to look them up in the Wazuh UI. However, we can find more detailed information and any related errors in the logs. If everything works fine, after restarting Wazuh we should find inside <WAZUH_HOME>/logs/ossec.log something similar to this:
2020/04/28 11:00:12 wazuh-modulesd:aws-s3: INFO: Module AWS started 2020/04/28 11:00:12 wazuh-modulesd:aws-s3: INFO: Starting fetching of logs. 2020/04/28 11:00:12 wazuh-modulesd:aws-s3: INFO: Executing Bucket Analysis: (Bucket: wazuh-aws-wodle, Path: macie, Type: custom, Profile: default) 2020/04/28 11:00:15 wazuh-modulesd:aws-s3: INFO: Fetching logs finished.
If there is an issue, for example if the credentials file is not found, you will get logs like these:
2020/04/28 10:45:13 wazuh-modulesd:aws-s3: INFO: Module AWS started 2020/04/28 10:45:13 wazuh-modulesd:aws-s3: INFO: Starting fetching of logs. 2020/04/28 10:45:13 wazuh-modulesd:aws-s3: INFO: Executing Bucket Analysis: (Bucket: wazuh-aws-wodle, Path: macie, Type: custom, Profile: default) 2020/04/28 10:45:14 wazuh-modulesd:aws-s3: WARNING: Bucket: - Returned exit code 12 2020/04/28 10:45:14 wazuh-modulesd:aws-s3: WARNING: Bucket: - The config profile (default) could not be found 2020/04/28 10:45:14 wazuh-modulesd:aws-s3: INFO: Fetching logs finished.
In this case you should make sure that the credentials are located in the path mentioned above, as well as that the format is correct. Keep in mind that errors are usually quite descriptive, allowing you to find the source of most problems.
If you need a higher level of verbosity, you can modify the file <WAZUH_HOME>/etc/local_internal_options.conf and add wazuh_modules.debug=2. After that, restart Wazuh again and check the ossec.log file.
Viewing AWS alerts in Kibana
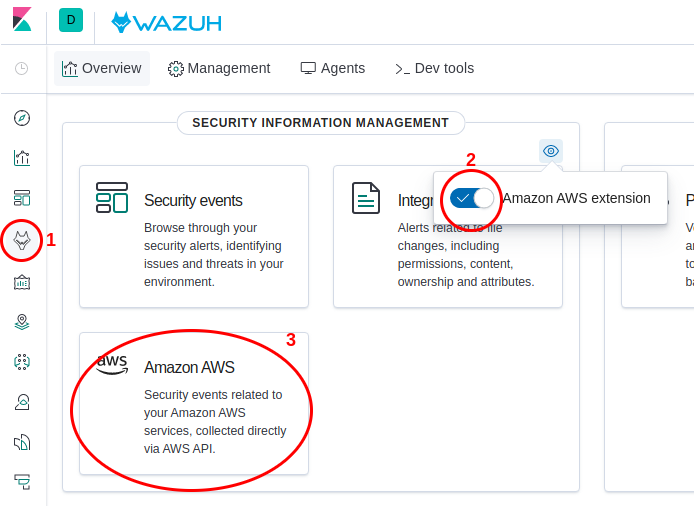
After you have successfully configured Wazuh to display Amazon Macie alerts, it’s time to open Wazuh UI in Kibana to view them. It is recommended to activate the Amazon AWS extension as seen in the image below. Thereby, you will have direct access to a summary of all your AWS activity. 
When accessing the panel of the Amazon AWS extension, we will find something similar to what is seen in the following image. At a glance, we will find graphs showing the sources of all alerts, the accounts to which they belong, the name of each bucket in which the logs are being stored and also graphs of events per second based on different criteria, among others things.
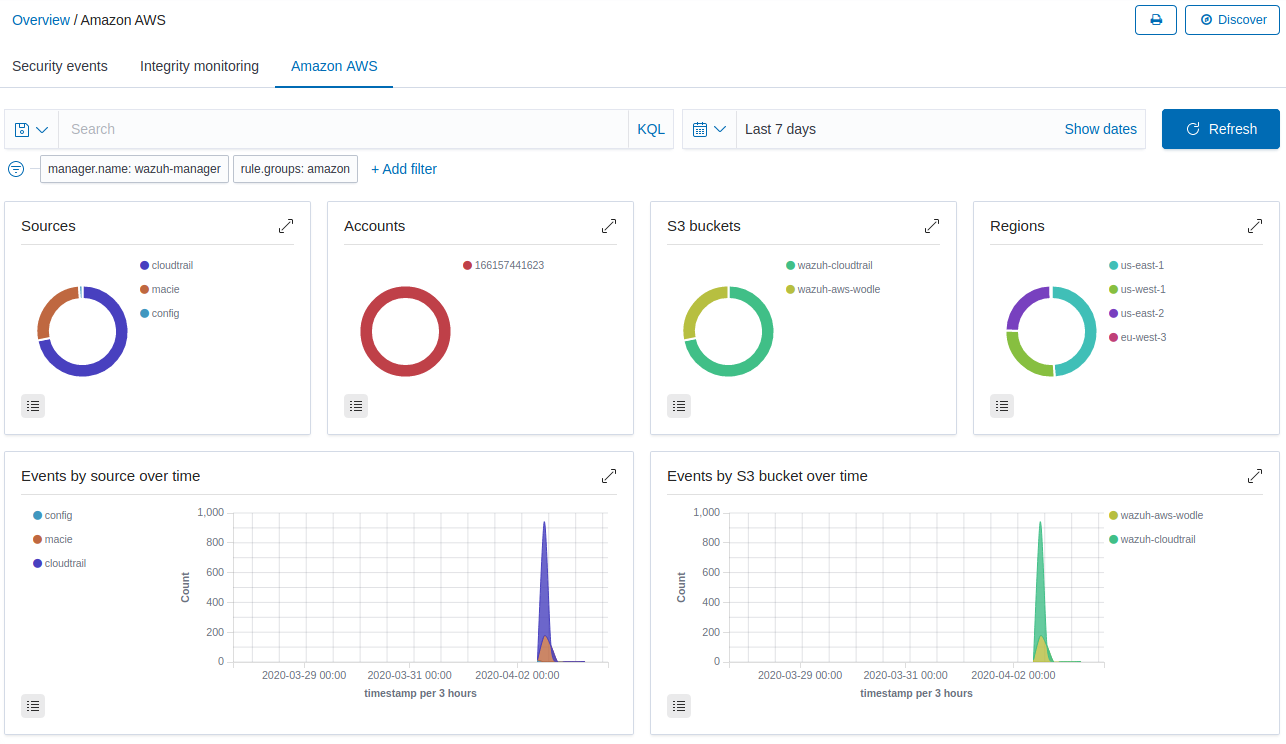
If we click on the section of the graph that corresponds to Macie, a filter will be added showing only those alerts whose source is Amazon Macie. After scrolling, we find a panel with alerts classified based on their occurrence. We can also access detailed information of each alert. To do it, just click on the button Discover in the upper right corner.
Use case: Denied role creation
There are many suspicious activities that Amazon Macie manages to identify and classify thanks to the use of machine learning, so these use cases are only a small set of interesting examples.
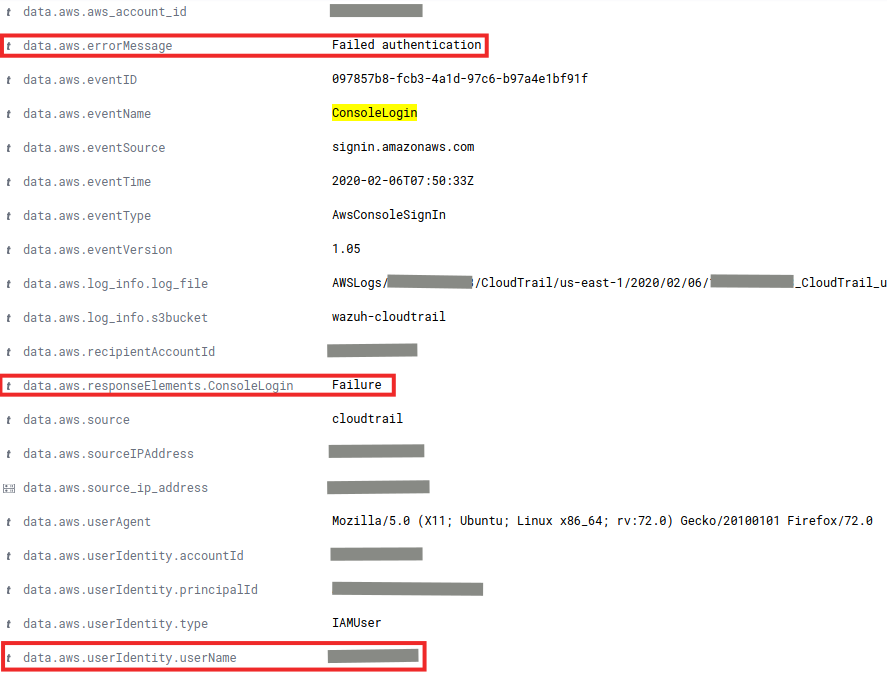
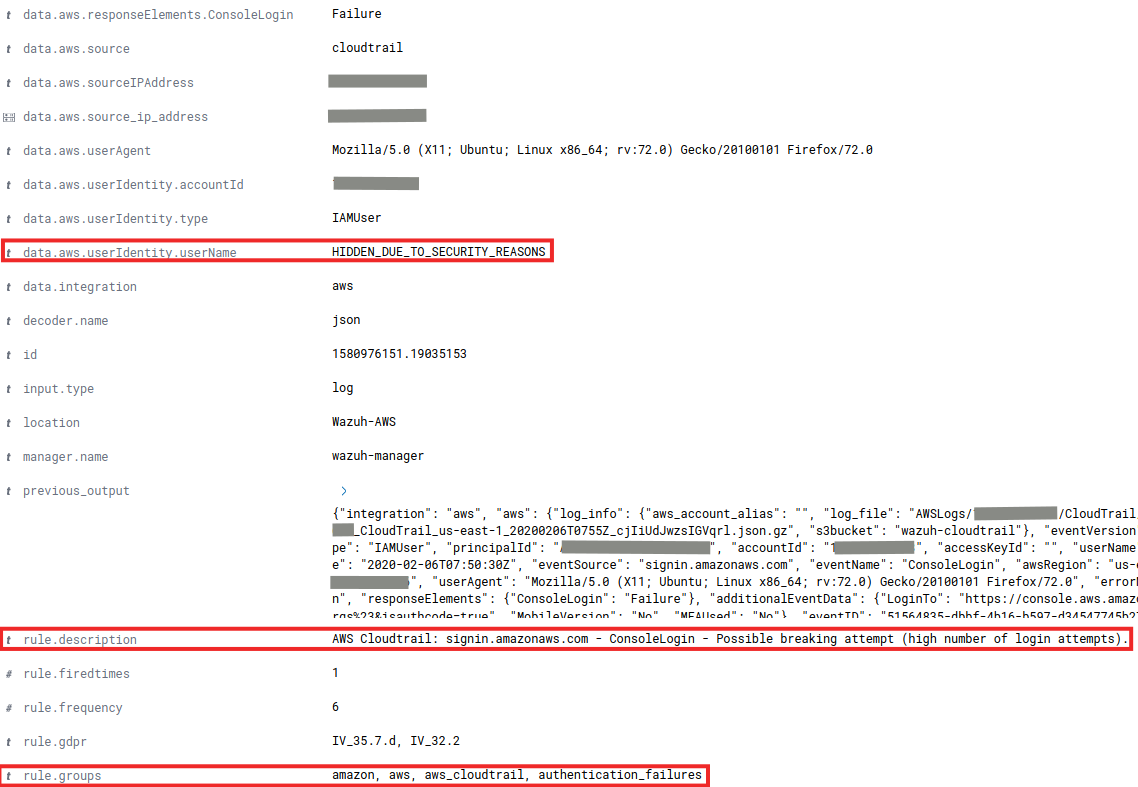
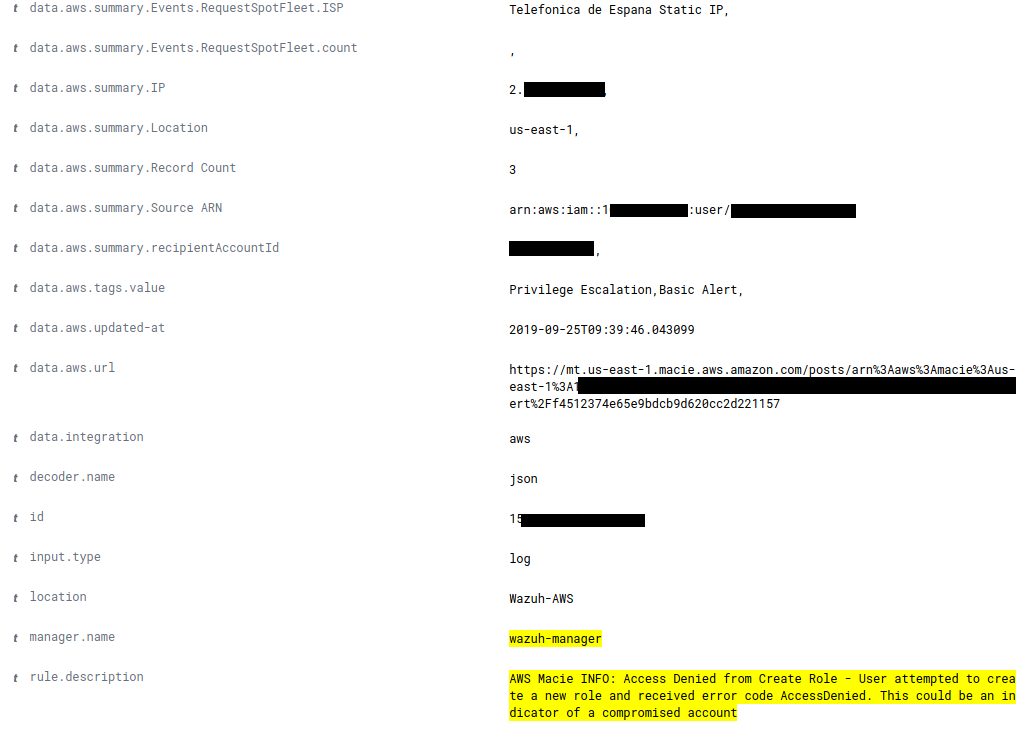
It is recommended to review all generated events (which is easier with the integration in Wazuh) to identify suspicious behavior such as the following, in which the creation of a new role has been denied. Modifying and creating roles is critically important as they define what actions a user can take. A new role could compromise the security of the data hosted on S3.
Use case: Increased number of accesses to S3
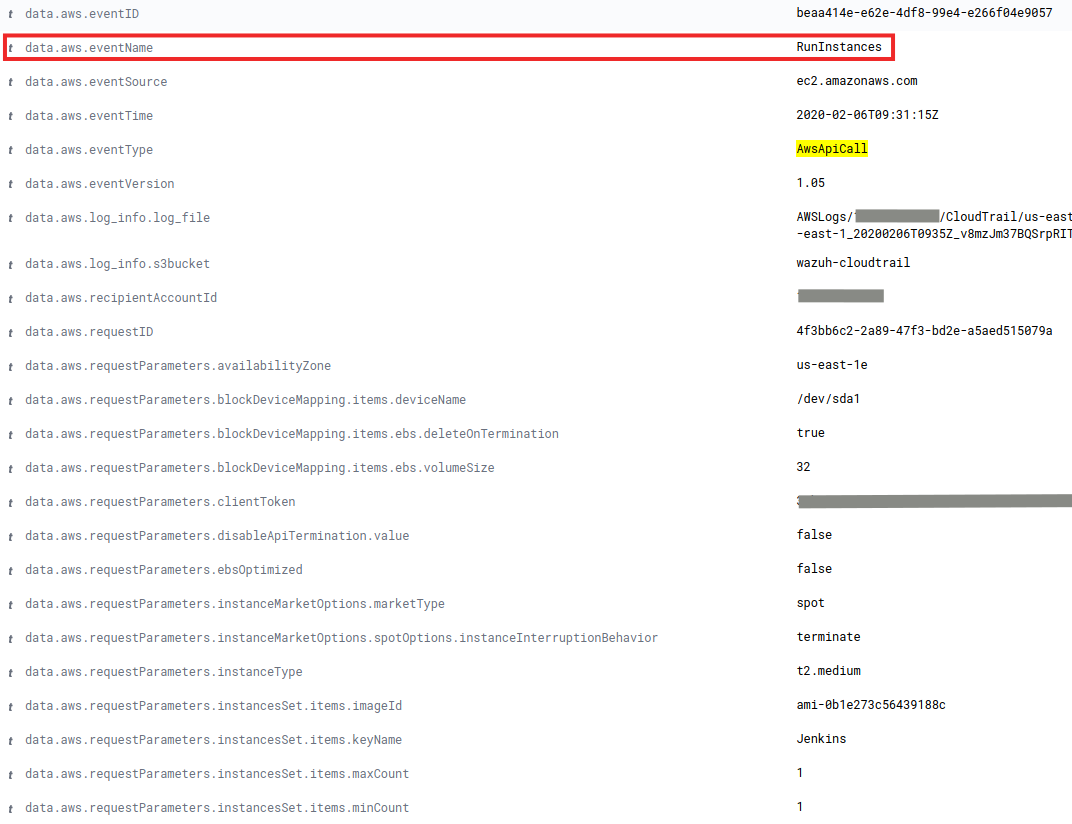
Macie also generates events when the pattern of access to buckets changes. These events are really useful since they could help us to identify early exposure of the stored data. And of course, to solve it in time.
It happens for example when a user who does not usually download anything, begins to download many files from the bucket, and also when the number of times that a bucket is read increases. This is the case of the following event:
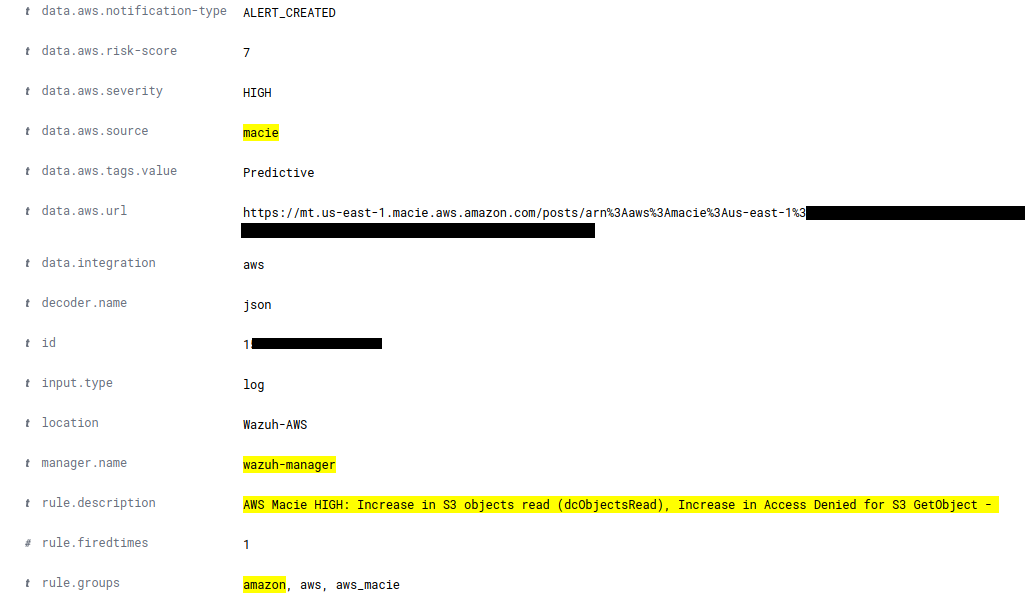
Conclusion
Having secure systems in which to store the information we generate is incredibly important nowadays. The leakage of personal or any other data can result not only in the loss of credibility of a company but also in significant financial penalties. Therefore, all efforts are justified when it comes to monitoring the correct processing of data.
We have seen that integrating Amazon Macie into Wazuh is really easy. After doing so, this and many other services will be centralized in one place, the Wazuh UI. Unified access to all the information gives us many advantages, such as a fast overview of everything that is happening (especially critical information), greater agility to find security risks, personalization of alerts and even automation of actions which may save us from a future headache.
References
- Using Wazuh to monitor AWS
- Wazuh Amazon Macie configuration
- Amazon Macie
- Amazon Macie official documentation
If you have any questions about this, don’t hesitate to check out our documentation to learn more about Wazuh. You can also join our Slack #community channel and our mailing list where our team and other users will help you with your questions.
The post Integrating Amazon Macie in Wazuh appeared first on Wazuh.