Products are tools that enable people to achieve goals. In order for products to be effective, the people managing them must implement and use them appropriately. This requires technical personnel and non-technical personnel to communicate effectively while working toward solving the same problem. Collaboration is key to mapping technical specifications to business functionality in an efficient manner.
The Open Group Architecture Framework (TOGAF)
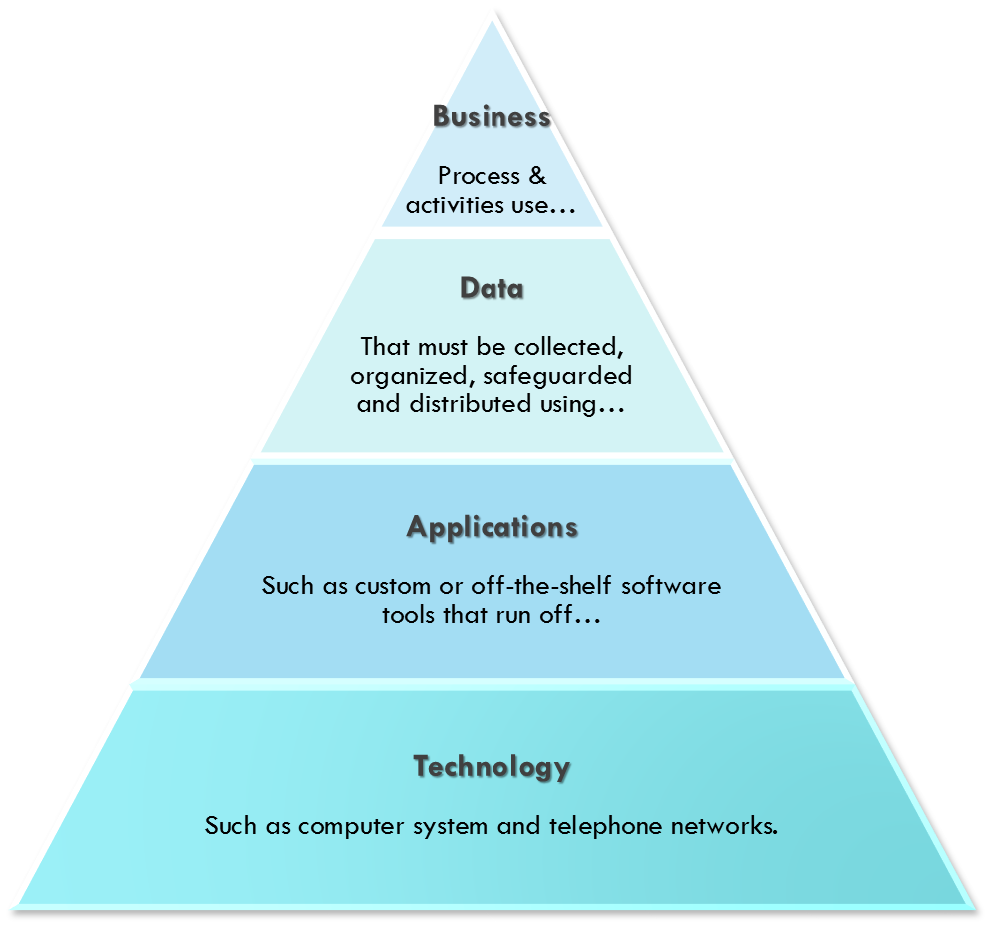
TOGAF has its origins in the U.S. Department of Defense. It provides an approach on how to design, implement, and govern an enterprise information architecture.
TOGAF is a framework that can be used to develop the following architecture types:
Endpoint security is the process of securing the various endpoints connected within your network, often defined as end-user devices such as mobile devices, laptops, and desktop PCs, although hardware such as servers in a data center are also considered endpoints. This is best practice as defined by all Security Compliances Frameworks such as PCI DSS, ISO 27001, and SSAE 16.
SSO and MFA
OKTA or Azure AD identity service improves end-user productivity and secures access to cloud, mobile and on-premises applications via single sign-on (SSO), user provisioning and multi-factor authentication (MFA). Okta supports internal users (employees, contractors) and external users (partners, customers), and manages applications, mobile devices, and Macs via Active Directory and LDAP. It can be deployed in the cloud or on-premises.
Crowdstrike (white box)
Fastest and most powerful turnkey MDR in the market includes full-cycle remediation and requires no additional personnel resourcing. CrowdStrike had the highest detection coverage out of all participants in 2022 MITRE ATT&CK Evaluation for Managed Services..
Malwarebytes (black box)
Malwarebytes Nebula Platform is a cloud-hosted security platform made for small to large businesses. Increase security without compromising productivity.
Sentinel (black box)
WebRoot (black box)
WebRoot SecureAnywhere® BusinessEndpoint Protection provides security for servers, VMs, PCs, and Mac devices and protection against infections and data theft without sacrificing performance or productivity.
Tines No-code automation for security teams can save analyst hours a week, allowing your teams and analysts to focus on higher priority tasks and new detection capabilities.
The world’s best companies – from startups to the Fortune 10 – trust Tines with their mission-critical security workflows.
Ansible
Ansible is a free software platform for configuring and managing computers. It combines multi-node software deployment, ad hoc task execution, and configuration management. It manages Linux nodes over SSH or Windows nodes over PowerShell.
LabTech
LabTech can take care of any repetitive IT maintenance task or process, monitor mission critical network components, run auto-remediation programs, and much more.T
Regardless of their longevity, any web application is vulnerable to security exploits. Robust IPS/IDS solutions such as those offered by Security Onion, Darktrace, and Netscope, will detect and block attempted attacks, and should be incorporated into a larger and layered security approach. Security Onion is quickly evolving and adding many new tools on a regular basis, thanks to its very active and growing user base. It is a distributed tool that allows any security analyst to configure and run an intrusion detection system with full monitoring and reporting capabilities in just a matter of minutes.
We provide Network Detection Systems Integrations with the features below
- Full Network Analysis
- PCI DSS Compliance Benchmarks
- Security Hardening Benchmarks
- Vulnerability Benchmarks
- Full Packet Capture Analysis-Driven Network Intrusion Detection
- Snort or Suricata Rule-Driven Intrusion Detection
- Real-time, Event-Driven Intrusion Detection
- Time-Based Alerting
- Threat Intelligence Feeds
ZeroKit
- Typically, hash-based user authentication is used, which is vulnerable to “pass the hash” attacks to log in on behalf of the users, simply using the stored password hash
- Password salts sometimes are stored with the hash in the user database, exposing the password database to brute force or dictionary attacks
- The secure web traffic (HTTPS) decrypts on the web server, exposing sensitive data in log files or to zero day exploits
- At-rest encryption stores the encryption key on disk or in a database, exposing sensitive data to hackers.
OSSEC/WAZUH
OSSEC/WAZUH is a free, open-source host-based intrusion detection system (HIDS). It performs log analysis, integrity checking, Windows registry monitoring, rootkit detection, time-based alerting, and active response. It provides intrusion detection for most operating systems, including Linux, OpenBSD, FreeBSD, OS X, Solaris and Windows. OSSEC/WAZUH has a centralized, cross-platform architecture allowing multiple systems to be easily monitored and managed.


