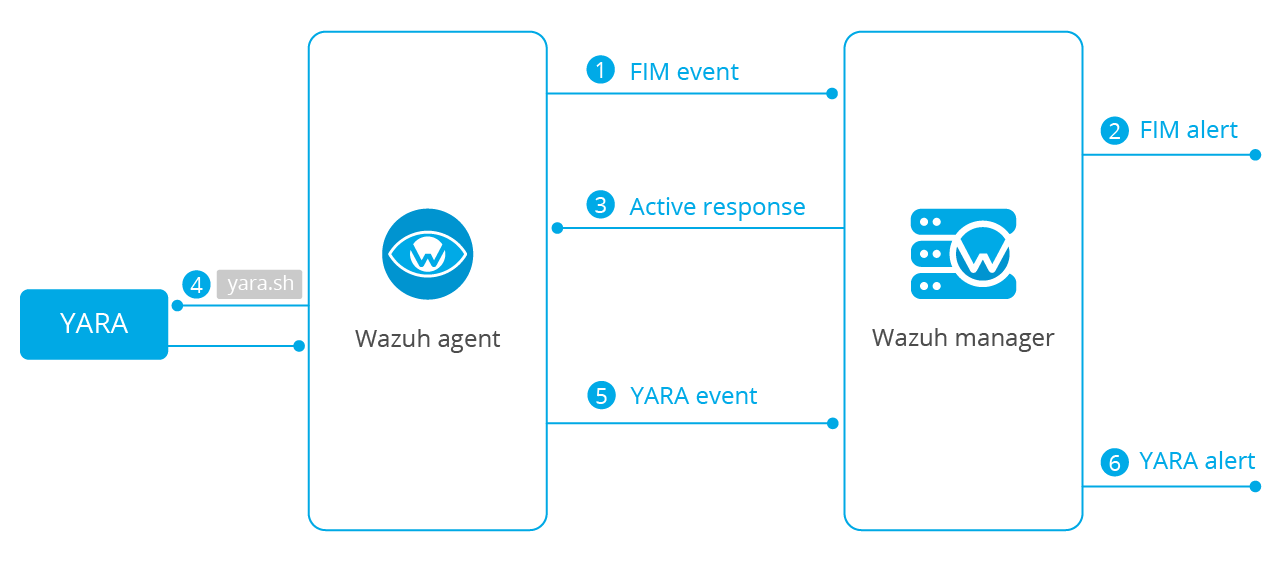
Wazuh can integrate with YARA in different ways. YARA is a versatile Open Source pattern-matching tool aimed to detect malware samples based on rule descriptions, although it is not limited to that use case alone.
This blog post will focus on automatically executing YARA scans by using the active response module when a Wazuh FIM alert is triggered.
This is an interesting way of using YARA as it concentrates the scans on new files or files that change in your environment, thus optimizing resource consumption on the monitored endpoints.
The next diagram illustrates the flow of events between the different components:
YARA rules
Rules consist of a set of strings to match and a boolean expression that determines its logic. Each rule starts with the keyword rule followed by an identifier. They are grouped in files that use the .yar extension.
The two most important sections inside a rule definition are:
Strings. This section defines the strings used in the rule. Each of them has an identifier consisting of a$character followed by a sequence of alphanumeric characters and underscores that you can later reference in the condition section. It is optional.Condition. A boolean expression that represents the logic of the rule. It is mandatory.
You can also provide a meta section used to specify comments or additional details about the rule.
This is a sample rule:
rule dummyRule
{
meta:
author = "your_author"
strings:
$text = "foo"
condition:
$text
}
Many resources regarding rule definitions are available on the Internet, including the following:
Strings
YARA offers three types of strings:
Hexadecimal. They are used for defining raw sequences of bytes, even allowing for wild-cards, jumps and alternatives.Text. A simple, case-sensitive string. You can apply modifiers that alter the way in which the string will be interpreted.Regular expressions. Perl-like syntax for regular expressions.
Example:
strings:
$hex_string = { E2 34 ?? C8 A? FB }
$text_string = "foobar"
$re_string = /state: (on|off)/
You can read here more about Yara Strings.
Condition
Generally, the condition will refer to previously defined strings by using their identifiers.
They contain the typical boolean and relational operators, but arithmetic and bitwise ones are also available.
Example:
condition:
$hex_string and ($text_string or $re_string)
You can read here more about conditions.
Note: You can distribute YARA rule files to groups of wazuh agents using the centralized configuration capability.
Wazuh active response
An active response can execute a script when a specific alert, alert level, or rule group is triggered in your Wazuh system. There are two types:
Stateful. It can undo the action after a specified period of time.Stateless. It represents a single execution without an event to revert the original effect.
You can also decide where the action will take place:
Local. It runs the script on the agent that generated the alert.Server. It runs the script on the Wazuh manager.Defined agent. You can specify the IDs of the agents that will run the script regardless of where the event has been observed.All. Every agent in the environment will run the script. Use with caution.
You can read here more about Wazuh active response.
For this blog post, you will define a stateless type of active response that will be executed locally on the agent that generated the alert.
Wazuh manager configuration
First, you need to tell the manager what is the action that you want to execute and under which circumstances you want it to be triggered. For that, edit the configuration file located at /var/ossec/etc/ossec.conf and add the following:
<ossec_config>
<command>
<name>yara</name>
<executable>yara.sh</executable>
<expect>filename</expect>
<extra_args>-yara_path /path/to/yara -yara_rules /path/to/rules</extra_args>
<timeout_allowed>no</timeout_allowed>
</command>
<active-response>
<command>yara</command>
<location>local</location>
<rules_id>550,554</rules_id>
</active-response>
</ossec_config>
Command
It contains information about the action to be executed on the agent, including its parameters:
- The
namesetting uniquely identifies the command,yara. - The script in the
executablesetting,yara.sh. - The
expectsetting lets you specify a field within the alert to pass on to the command. In this case the path to the file that triggered the FIM alert. - You also need to specify where the YARA binary and rules are located. For this you can use the
extra_argssetting. - The
timeout_allowedsetting set to no. This represents a stateless active response.
Active response
It defines the criteria used to execute a specific command:
- The
commandto execute. It references theyaracommand created above. - The
locationsetting aslocal. It means that the active response will be executed on the agent that generates the alert. - You can write a list of rule ids that will trigger the active response in the
rules_idsetting. This example uses rule550, new file added to the system, and rule554, file modified in the system.
Rules and decoders
Now you need to define a set of rules and decoders to trigger alerts from the events generated by the YARA active response.
Create a decoder file, for example /var/ossec/etc/decoders/yara_decoders.xml, and add the following:
<!-- - YARA decoders - Created by Wazuh, Inc. - Copyright (C) 2015-2020, Wazuh Inc. - This program is a free software; you can redistribute it and/or modify it under the terms of GPLv2. --> <decoder name="yara"> <prematch>wazuh-yara: </prematch> </decoder> <decoder name="yara"> <parent>yara</parent> <regex offset="after_parent">info: (S+) (.+)</regex> <order>yara_rule, file_path</order> </decoder> <decoder name="yara"> <parent>yara</parent> <regex offset="after_parent">error: (.+)</regex> <order>error_message</order> </decoder>
Similarly create a rule file, /var/ossec/etc/rules/yara_rules.xml, with the following content:
<!--
- YARA rules
- Created by Wazuh, Inc.
- Copyright (C) 2015-2020, Wazuh Inc.
- This program is a free software; you can redistribute it and/or modify it under the terms of GPLv2.
-->
<group name="yara,">
<rule id="100100" level="0">
<decoded_as>yara</decoded_as>
<description>YARA rules grouped.</description>
</rule>
<rule id="100101" level="5">
<if_sid>100100</if_sid>
<field name="error_message">.+</field>
<description>YARA error detected.</description>
</rule>
<rule id="100102" level="10">
<if_sid>100100</if_sid>
<field name="yara_rule">.+</field>
<description>YARA $(yara_rule) detected.</description>
</rule>
</group>
Wazuh agent configuration
The following section assumes YARA is already installed on the monitored endpoint. You can follow the official installation guide.
The script configured to run as part of the active response settings defined on the Wazuh manager, yara.sh, needs to be placed under /var/ossec/active-response/bin on the Wazuh agent side. Add the following content to it:
#!/bin/bash
# Wazuh - YARA active response
# Copyright (C) 2015-2020, Wazuh Inc.
#
# This program is free software; you can redistribute it
# and/or modify it under the terms of the GNU General Public
# License (version 2) as published by the FSF - Free Software
# Foundation.
#------------------------- Gather parameters -------------------------#
# Static active response parameters
FILENAME=$8
LOCAL=`dirname $0`
# Extra arguments
YARA_PATH=
YARA_RULES=
while [ "$1" != "" ]; do
case $1 in
-yara_path) shift
YARA_PATH=$1
;;
-yara_rules) shift
YARA_RULES=$1
;;
* ) shift
esac
shift
done
# Move to the active response folder
cd $LOCAL
cd ../
# Set LOG_FILE path
PWD=`pwd`
LOG_FILE="${PWD}/../logs/active-responses.log"
#----------------------- Analyze parameters -----------------------#
if [[ ! $YARA_PATH ]] || [[ ! $YARA_RULES ]]
then
echo "wazuh-yara: error: Yara path and rules parameters are mandatory." >> ${LOG_FILE}
exit
fi
#------------------------- Main workflow --------------------------#
# Execute YARA scan on the specified filename
yara_output=$(${YARA_PATH}/yara -w -r $YARA_RULES $FILENAME)
if [[ $yara_output != "" ]]
then
# Iterate every detected rule and append it to the LOG_FILE
while read -r line; do
echo "wazuh-yara: info: $line" >> ${LOG_FILE}
done <<< "$yara_output"
fi
exit 1;
Note: Make sure that the
yara.shfile ownership isroot:ossecand the permissions are750.
The script receives:
- The file path contained in the alert that triggered the active response in the
8th argument. -yara_path. Path to the folder where the Yara executable is located; by default this is usually/usr/local/bin.-yara_rules. File path to the Yara rules file used for the scan.
It uses the parameters above to perform a YARA scan:
# Execute YARA scan on the specified filename
yara_output=$(${YARA_PATH}/yara -w -r $YARA_RULES $FILENAME)
Then it analyzes the output to determine if the scan triggered any YARA rule:
# Iterate every detected rule and append it to the LOG_FILE
while read -r line; do
echo "wazuh-yara: $line" >> ${LOG_FILE}
done <<< "$yara_output"
For every line in the output, the script will append an event to the active response log, /var/ossec/logs/active-responses.log, with the following format:
wazuh-yara: info: yara_rule file_path
Note: There’s no need to configure the agent to monitor the active response log as it is part of the agent’s default configuration.
Malware detection use case
HiddenWasp is a sophisticated malware that infects Linux systems, used for targeted remote control. Its authors took advantage of various publicly available Open Source malware, such as Mirai and Azazel rootkit.
It has three different components:
Deployment script. Initial attack vector.Rootkit. Artifact hiding mechanisms and TCP connection hiding.Trojan. C&C requests.
You can read here a thorough analysis of this malware.
Deployment script
It is typically a bash script that tries to download the malware itself by connecting to an SFTP server. This script even updates the malware if the host was already compromised.
The main IoCs to look for in this component are the IP and files that it copies to the system:
rule HiddenWasp_Deployment
{
strings:
$a = "http://103.206.123.13:8080/configUpdate.tar.gz"
$b = "http://103.206.123.13:8080/configUpdate-32.tar.gz"
$c = "http://103.206.123.13:8080/system.tar.gz"
$d = "103.206.123.13"
condition:
any of them
}
Rootkit
User-space based rootkit enforced via the LD_PRELOAD Linux mechanism, and delivered as an ET_DYN stripped ELF binary. It tries to hide the trojan part of the malware by cloaking artifacts and TCP connections.
The following YARA rule detects its signature by using hexadecimal strings:
rule HiddenWasp_Rootkit
{
strings:
$a1 = { FF D? 89 ?? ?? 83 ?? ?? ?? 0F 84 [0-128] BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? B8 ?? ?? ?? ?? FF D? 48 ?? ?? ?? 48 ?? ?? ?? ?? 74 [0-128] C6 ?? ?? ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? BE ?? ?? ?? ?? }
$a2 = { 0F 84 [0-128] BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? B8 ?? ?? ?? ?? FF D? }
$a3 = { 0F B6 ?? 83 ?? ?? 88 ?? 83 [0-128] 8B ?? ?? 3B ?? ?? 0F 82 [0-128] 48 ?? ?? ?? 48 }
$a4 = { 74 [0-128] C6 ?? ?? ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? BE ?? ?? ?? ?? B8 ?? ?? ?? ?? E8 ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? BF ?? ?? ?? ?? B8 ?? ?? ?? ?? FF D? 89 ?? ?? 83 ?? ?? ?? 0F 84 [0-128] BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? B8 ?? ?? ?? ?? FF D? }
$b0 = { E8 ?? ?? ?? ?? 83 ?? ?? 83 ?? ?? FF B? ?? ?? ?? ?? E8 ?? ?? ?? ?? 83 [0-128] C6 ?? ?? ?? ?? ?? ?? FF 7? ?? 83 ?? ?? 6A ?? E8 ?? ?? ?? ?? 83 ?? ?? 5? 68 ?? ?? ?? ?? 8D ?? ?? ?? ?? ?? 5? E8 ?? ?? ?? ?? 83 ?? ?? 83 ?? ?? 83 ?? ?? 6A ?? E8 ?? ?? ?? ?? 83 ?? ?? 89 ?? 8D ?? ?? 5? 8D ?? ?? ?? ?? ?? 5? 6A ?? FF D? 83 ?? ?? 89 ?? ?? 83 ?? ?? ?? 0F 84 [0-128] 83 ?? ?? 83 ?? ?? 6A ?? E8 ?? ?? ?? ?? 83 ?? ?? 8D ?? ?? ?? ?? ?? 5? 8D ?? ?? ?? ?? ?? 5? FF D? 83}
$b1 = { 83 ?? ?? 83 ?? ?? 6A ?? E8 ?? ?? ?? ?? 83 ?? ?? 89 ?? 8D ?? ?? 5? FF 7? ?? 6A ?? FF D? 83 ?? ?? 89 ?? ?? 83 ?? ?? ?? 0F 84 [0-128] 83 ?? ?? 68 ?? ?? ?? ?? E8 ?? ?? ?? ?? 83 ?? ?? 89 ?? ?? ?? ?? ?? C6 ?? ?? ?? ?? ?? ?? FF 7? ?? 83 ?? ?? 6A ?? E8 ?? ?? ?? ?? 83 ?? ?? 5? 68 ?? ?? ?? ?? 8D ?? ?? ?? ?? ?? 5? E8 ?? ?? ?? ?? 83 ?? ?? 83 ?? ?? 83 ?? ?? 6A ?? E8 ?? ?? ?? ?? 83 ?? ?? 89 ?? 8D ?? ?? 5? }
$b2 = { 8B ?? ?? 8B ?? ?? 29 ?? 89 ?? 8B ?? ?? F7 ?? 21 ?? 23 ?? ?? 85 ?? 74 [0-128] 8B ?? ?? 83 ?? ?? 89 ?? ?? 8B ?? ?? 80 3? ?? 75 [0-128] 8B ?? ?? 8B ?? ?? 29}
$b3 = { 8B ?? ?? 29 ?? 89 ?? 8B ?? ?? F7 ?? 21 ?? 23 ?? ?? 85 ?? 74 [0-128] 8B ?? ?? 83 ?? ?? 89 ?? ?? 8B ?? ?? 80 3? ?? 75 [0-128] 8B}
$b4 = { 83 ?? ?? 8B ?? ?? 89 ?? ?? 8B ?? ?? 89 [0-128] 8B ?? ?? 89 ?? 8D ?? ?? FF 0? 8A ?? 88 ?? ?? 8B ?? ?? 89 ?? 8D ?? ?? FF 0? 8A ?? 88 ?? ?? 80 7? ?? ?? 75 [0-128] 8A ?? ??}
condition:
all of ($a*) or all of ($b*)
}
Trojan
Statically linked ELF binary that uses the stdlibc++. Its main goal is to allow the C&C requests sent by the clients that connect to it.
Similarly to the rootkit, this YARA rule contains hexadecimal strings that can detect this component’s binary signature:
rule HiddenWasp_Trojan
{
strings:
$a0 = { 5? 5? 5? E8 ?? ?? ?? ?? 8B ?? ?? 29 ?? 89 ?? ?? 89 ?? ?? 8B ?? ?? 8B ?? ?? 29 ?? ?? 29 ?? ?? 83 ?? ?? 8B ?? ?? 8D ?? ?? 89 [0-128] 83 ?? ?? 0F B7 }
$a1 = { 31 ?? 89 [0-128] FC 88 ?? 89 ?? 89 ?? F2 ?? F7 ?? 4? 66 ?? ?? ?? ?? ?? C6 ?? ?? ?? ?? 89 ?? 89 ?? F2 ?? F7 ?? 4? 89 ?? ?? ?? ?? ?? 8B ?? ?? ?? ?? ?? 89 ?? F2 ?? F7 ?? 4? 39 ?? ?? ?? ?? ?? 75 [0-128] BB ?? ?? ?? ?? 31 ?? FC 8B ?? ?? ?? ?? ?? 88 ?? 89 ?? F2 ?? F7 ?? 89 ?? ?? ?? ?? ?? 8B ?? ?? 89 ?? F2 ?? F7 ?? 8D ?? ?? ?? 8B ?? ?? ?? ?? ?? 8D ?? ?? ?? 89 ?? ?? ?? ?? ?? 88 ?? 89 ?? 89 ?? F2 ?? 8B ?? ?? ?? ?? ?? F7 ?? 8D ?? ?? ?? ?? ?? ?? 83 ?? ?? 5? E8 ?? ?? ?? ?? 5? 5? FF 7? ?? FF 7? ?? FF 7? ?? FF 7? ?? FF 7? ?? 5? }
$a2 = { FF B? ?? ?? ?? ?? E8 ?? ?? ?? ?? 83 ?? ?? 85 ?? 74 [0-128] 8D ?? ?? FC 89 ?? BF ?? ?? ?? ?? B9 ?? ?? ?? ?? F3 ?? 75 [0-128] 8B ?? ?? ?? ?? ?? 8B ?? 89 ?? ?? ?? ?? ?? 31 ?? 8B ?? ?? ?? ?? ?? B9 ?? ?? ?? ?? F2 ?? 89 ?? 89 ?? B9 ?? ?? ?? ?? F2 ?? F7 ?? F7 ?? 83 ?? ?? 8D ?? ?? ?? 5? E8 ?? ?? ?? ?? }
$a3 = { 5? E8 ?? ?? ?? ?? 83 ?? ?? 5? E8 ?? ?? ?? ?? 5? 5? 5? 8D ?? ?? ?? ?? ?? 5? E8 ?? ?? ?? ?? 8D ?? ?? ?? ?? ?? 8D ?? ?? 89 ?? ?? 5? E8 ?? ?? ?? ?? 8B ?? ?? ?? ?? ?? 8D ?? ?? B9 ?? ?? ?? ?? 83 ?? ?? 39 ?? 0F 85 [0-128] 83 ?? ?? 68 ?? ?? ?? ?? 83 ?? ?? 68 ?? ?? ?? ?? 5? E8 ?? ?? ?? ?? 83 ?? ?? 5? }
$a4 = { C6 ?? ?? ?? C6 ?? ?? ?? ?? C6 ?? ?? ?? ?? 8B ?? ?? FC 31 ?? B9 ?? ?? ?? ?? F2 ?? 31 ?? F7 ?? 4? 89 ?? 8D ?? ?? ?? ?? ?? 89 ?? ?? ?? ?? ?? 39 ?? 66 ?? 88 ?? AA 7D [0-128] 8B ?? ?? ?? ?? ?? C6 ?? ?? ?? C6 ?? ?? ?? ?? C6 ?? ?? ?? ?? BB ?? ?? ?? ?? 31 ?? FC 89 ?? 89 ?? F2 ?? 89 ?? 8B ?? ?? ?? ?? ?? 89 ?? F2 ?? F7 ?? F7 ?? }
$a5 = { 81 E? ?? ?? ?? ?? 31 ?? BE ?? ?? ?? ?? FC 88 ?? 8B ?? ?? ?? ?? ?? 89 ?? F2 ?? 89 ?? 8B ?? ?? ?? ?? ?? 89 ?? F2 ?? F7 ?? F7 ?? 8D ?? ?? ?? 5? E8 ?? ?? ?? ?? FF 3? ?? ?? ?? ?? FF 3? ?? ?? ?? ?? 68 ?? ?? ?? ?? 5? 89 ?? E8 ?? ?? ?? ?? 83 ?? ?? 68 ?? ?? ?? ?? 5? E8 ?? ?? ?? ?? 83 ?? ?? 85 ?? 89 ?? 74 [0-128] 5? 68 }
$a6 = { 0F 86 [0-128] 31 ?? 83 ?? ?? ?? 0F 86 [0-128] 8B ?? ?? 8B ?? ?? 8B ?? ?? 8B ?? ?? 8B ?? ?? 0F B6 ?? ?? ?? D3 ?? 31 ?? 8B ?? ?? 23 ?? ?? 8B ?? ?? 89 ?? ?? 8B ?? ?? 0F B7 ?? ?? 89 ?? ?? }
$b0 = { EB [0-128] 8B ?? ?? 3B ?? ?? 7C [0-128] 48 ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? ?? 48 ?? ?? BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? }
$b1 = { ?? 48 ?? ?? ?? BE ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? BA ?? ?? ?? ?? BE ?? ?? ?? ?? BF ?? ?? ?? ?? B8 ?? ?? ?? ?? E8 ?? ?? ?? ?? 89 ?? ?? 8B ?? ?? E8 ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? E8 ?? ?? ?? ?? E8 ?? ?? ?? ?? 89 ?? 8B ?? ?? 39 ?? 75 [0-128] E8 ?? ?? ?? ?? 83 ?? ?? 74 [0-128] 48 }
$b2 = { 75 [0-128] 48 ?? ?? ?? ?? ?? ?? BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? B8 ?? ?? ?? ?? FC 48 ?? ?? ?? F2 ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? BA ?? ?? ?? ?? E8 ?? ?? ?? ?? 89 ?? ?? 83 ?? ?? ?? 79 [0-128] 48 }
$b3 = { ?? ?? ?? BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? B8 ?? ?? ?? ?? FC 48 ?? ?? ?? F2 ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? BA ?? ?? ?? ?? E8 ?? ?? ?? ?? 89 ?? ?? 83 ?? ?? ?? 79 [0-128] 48 ?? ?? ?? E8 ?? }
$b4 = { 0F B6 ?? 48 ?? ?? ?? BE ?? ?? ?? ?? B8 ?? ?? ?? ?? E8 ?? ?? ?? ?? 8B ?? ?? 01 ?? 48 ?? 48 ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 0F B7 ?? 66 ?? ?? 83 [0-128] 8B ?? ?? 3B ?? ?? 7C [0-128] 8B ?? ?? 01 ?? 48 ?? 48 ?? ?? ?? C6 ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 8B ?? ?? 01 ?? 48 ?? 48 ?? ?? ?? C6 ?? ?? 48 ?? ?? ?? }
$b5 = { ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? B8 ?? ?? ?? ?? FC 48 ?? ?? ?? ?? ?? ?? F2 ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? B8 ?? ?? ?? ?? FC 48 ?? ?? ?? ?? ?? ?? F2 ?? 48 ?? ?? 48 ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? ?? ?? ?? 48 ?? ?? ?? BE ?? ?? ?? ?? B8 ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 ?? ?? ?? 48 ?? ?? ?? ?? 75 [0-128] 48 ?? ?? ?? ?? ?? ?? BA ?? }
condition:
all of ($a*) or all of ($b*)
}
Wazuh alerts
The YARA rules above generate these alerts when executed through the Wazuh active response:
{
"timestamp": "2020-06-09T08:15:07.187+0000",
"rule": {
"level": 10,
"description": "YARA HiddenWasp_Deployment detected.",
"id": "100102",
"firedtimes": 1,
"mail": false,
"groups": ["yara"]
},
"agent": {
"id": "001",
"name": "yara-agent",
"ip": "10.0.2.x"
},
"manager": {
"name": "wazuh-manager"
},
"id": "1591690507.38027",
"full_log": "wazuh-yara: info: HiddenWasp_Deployment /home/user/script.sh",
"decoder": {
"name": "yara"
},
"data": {
"yara_rule": "HiddenWasp_Deployment",
"file_path": "/home/user/script.sh"
},
"location": "/var/ossec/logs/active-responses.log"
}
{
"timestamp": "2020-06-09T08:18:47.901+0000",
"rule": {
"level": 10,
"description": "YARA HiddenWasp_Rootkit detected.",
"id": "100102",
"firedtimes": 1,
"mail": false,
"groups": ["yara"]
},
"agent": {
"id": "001",
"name": "yara-agent",
"ip": "10.0.2.x"
},
"manager": {
"name": "wazuh-manager"
},
"id": "1591690407.33120",
"full_log": "wazuh-yara: info: HiddenWasp_Rootkit /home/user/binary",
"decoder": {
"name": "yara"
},
"data": {
"yara_rule": "HiddenWasp_Rootkit",
"file_path": "/home/user/binary"
},
"location": "/var/ossec/logs/active-responses.log"
}
{
"timestamp": "2020-06-09T11:10:01.229+0000",
"rule": {
"level": 10,
"description": "YARA HiddenWasp_Trojan detected.",
"id": "100102",
"firedtimes": 1,
"mail": false,
"groups": ["yara"]
},
"agent": {
"id": "001",
"name": "yara-agent",
"ip": "10.0.2.x"
},
"manager": {
"name": "wazuh-manager"
},
"id": "1591701001.39854",
"full_log": "wazuh-yara: info: HiddenWasp_Trojan /home/user/another_binary",
"decoder": {
"name": "yara"
},
"data": {
"yara_rule": "HiddenWasp_Trojan",
"file_path": "/home/user/another_binary"
},
"location": "/var/ossec/logs/active-responses.log"
}
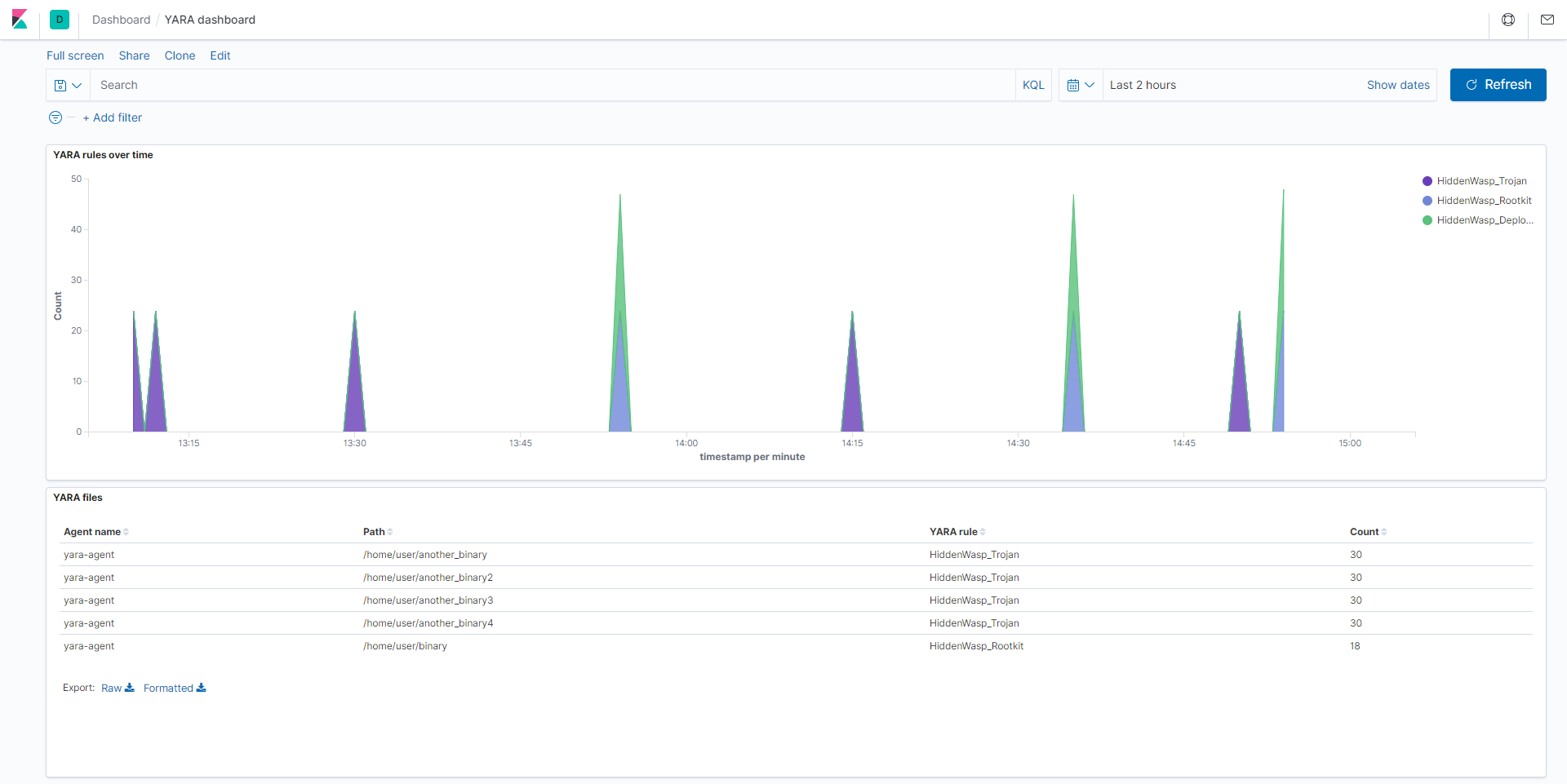
You can also create custom dashboards in Kibana for this integration:
Conclusion
The Wazuh active response module lets you react on any type of alert triggered in the system, creating very powerful behaviors.
In this case, you are taking advantage of Wazuh FIM, using it almost as a high-level heuristic to signal which files should be scanned by YARA, saving time and resources in the process.
References
- YARA rule strings.
- YARA rule conditions.
- GitHub Yara-Rules repository.
- Valhalla rules.
- Wazuh agent groups.
- Wazuh active response.
- YARA installation guide.
- HiddenWasp analysis.
If you have any questions about this, join our Slack community channel! Our team and other contributors will help you.
The post How to integrate YARA with Wazuh appeared first on Wazuh.